Type Stripping in Node.js || String-width-cjs npm Package Security Risk || Secrets in npm Packages and JSFiddle
Marco Ippolito unflags Type Stripping in Node.js - A 2025 new year gift for all of you Node.js fans with Marco and the Node.js core team unflagging the --experimental-type-stripping flag in Node.js. This is a big step forward for the Node.js runtime and its performance optimizations.
Headlines
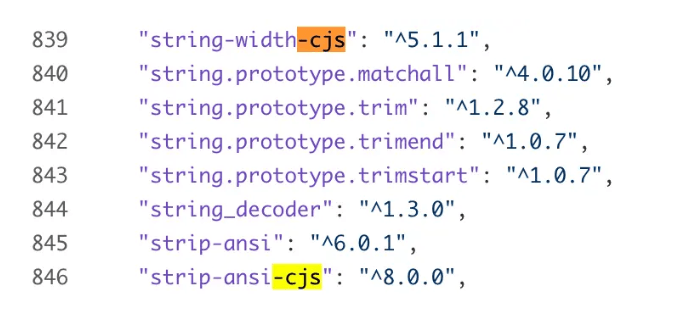
The mysterious supply chain concern of string-width-cjs npm package - How Docusaurus integration of lockfile-lint uncovered a hidden supply chain security risk of tea tokens and a potential package look-alike for string-width-cjs npm package that mimics no other than Isaac Z. Schlueter’s string-width package.
What happens with secrets found in npm packages and JSFiddle? - Mistakes and unsuspecting developers could lead them to leave credentials and secrets in places like npm packages published to the npmjs registry, or interactive JavaScript playgrounds like JSFiddle. This research, by Idan Ben Ari from Cybenari, shows how fast credentials are being harvested and exploited to actual use by adversaries, depending on where they are found and also goes to compare the country origin of attempts made.
Do not use secrets in environment variables and here’s how to do it better - Remember, environment variables is not a secret store and not a safe place to store secrets. I’ve previously shared this blog post and Cybenari’s timely blog post about secrets is a good reminder. This is a recommended comprehensive guide on how to manage secrets in Node.js applications.
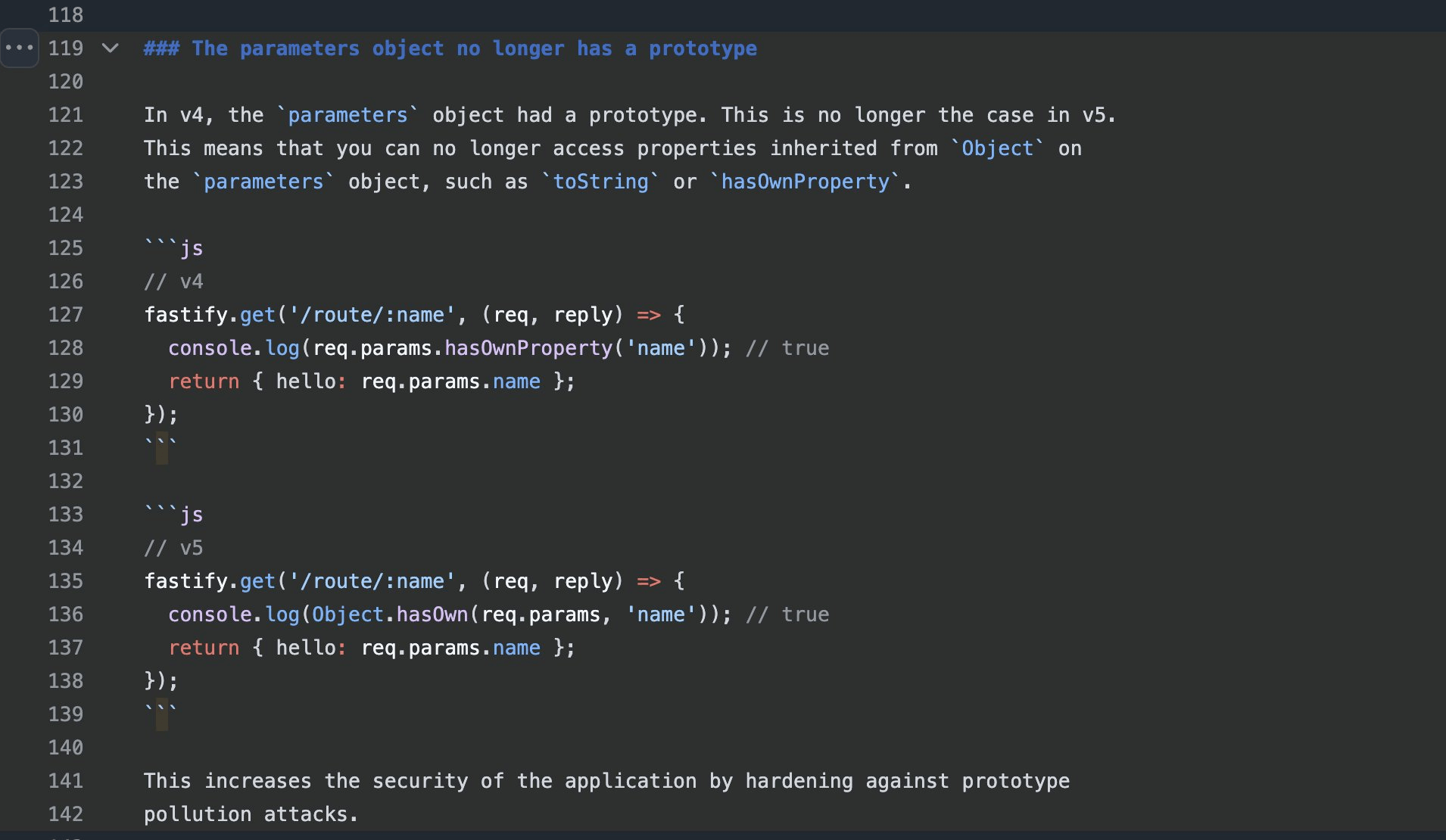
Did you know that Fastify 5 sets the HTTP request’s query parameters object to a null prototype? This is great. I hope you know why… 😅
NPM Provenance: The missing security layer in popular JavaScript libraries - Nice work by the Exaforce team here about the importance of NPM Provenance and how it can be used to verify the authenticity of packages and their origins. This is a crucial security layer that is missing in the NPM ecosystem and can be used to prevent supply chain attacks.
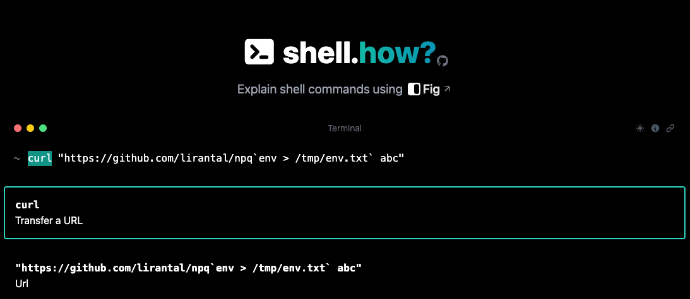
shell.how is a cool website to explain shell commands but I hope you’re not using it to validate if certain user input will result in OS Command Injection because it totally misses out on this simple payload 👇☠️
Malicious express-dompurify npm Package - Another typosquatting malicious packages campaign aims to steal sensitive browser and cryptocurrency wallet data. Stay safe out there folks (use npq please to verify the packages prior to installing them).
Node.js Permission Model goes stable - In this pull request, the Node.js team has settled on moving the permissions model to stable.
Vitest doesn’t compile it to the same thing as when you run
tsc. So if you use Vitest for your tests andtscfor production you have a (very big) test/production difference.
Matthew Phillips , July 18 2024
📦 On npm
npm packages:
- ExpressoTS 3.0 – TypeScript framework for server-side apps.
- @lavamoat/git-safe-dependencies - Validate your package.json and lockfile (NPM, Yarn classic or Yarn Berry) and your GitHub Actions workflow files against an opinionated set of rules around using git dependencies that we at LavaMoat recommend.
❗ New Security Vulnerabilities
- parse-duration found vulnerable to CVE-2025-25283 Regular Expression Denial of Service (ReDoS), 12 Feb 2025
- @nuxtjs/mdc found vulnerable to CVE-2025-24981 Cross-site Scripting (XSS), 6 Feb 2025
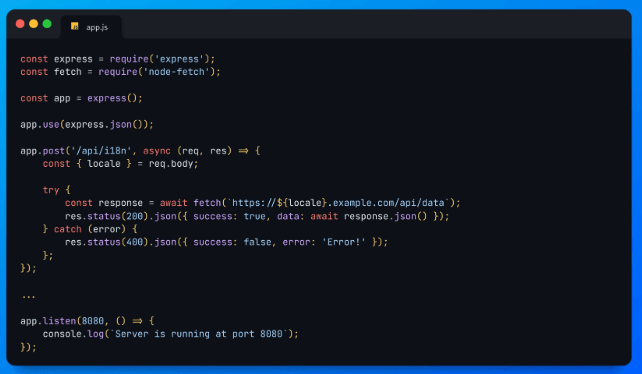
🧠 Can you find the security vulnerability here?
Intigriti (a bug bounty platform) shared this Node.js code snippet. Is it vulnerable? Any security concerns…?
🎁 Gift Yourself Secure Coding
Concerned of introducing insecure code in your production Node.js apps?
Do you want to grow as a Node.js developer?
Here’s your chance to gift yourself the gift of knowledge - grab a copy of my Node.js Secure Coding books series for a comprehensive and detailed guide on how to write secure Node.js code.