NPM Supply Chain Security || Prisma ORM Security || Fun Node.js Security Challenges
Headlines
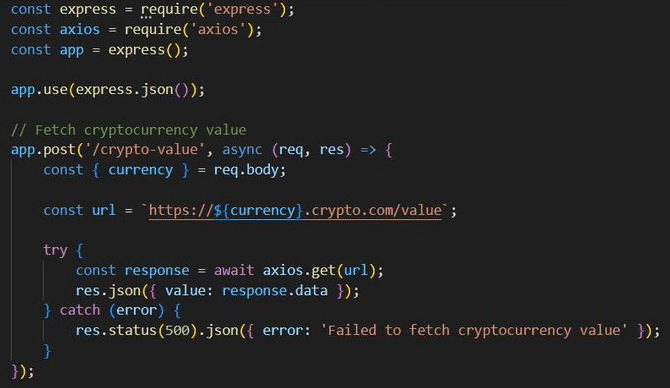
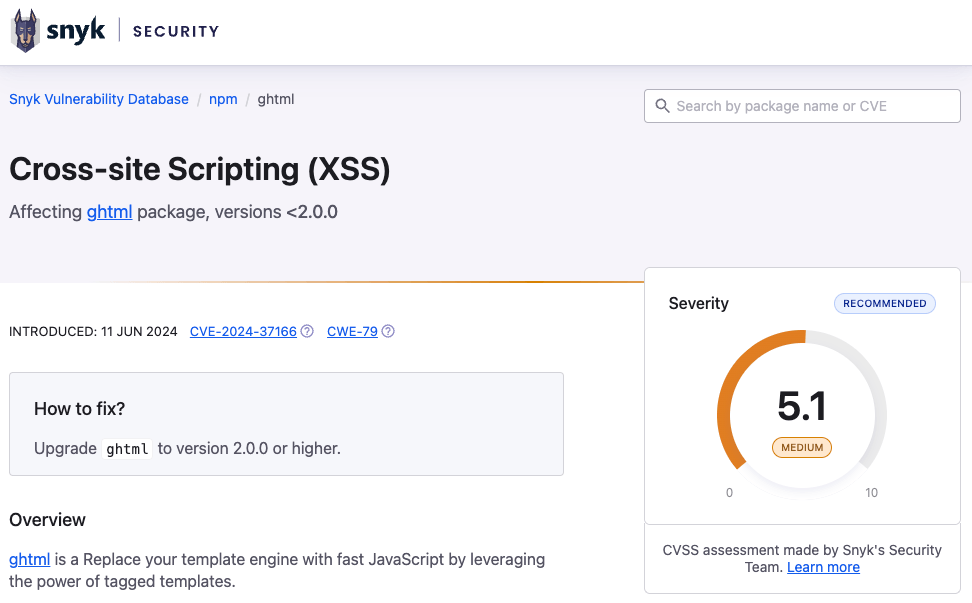
I found a vulnerability in ghtml - This finding is for an XSS attack vector for ghtml and @gurgunday/html which are npm packages proposing to be a fast JavaScript template engine. I recommend deep-diving into the vulnerability report if you want to learn about Cross-site Scripting in HTML templating engines 🕵️♀️
npm binary planting - A come back from a security issue reported to the npm team back at 2019, demonstrating how unsuspecting developers can be tricked to install malicious packages when trying to execute scripts with npx <bin-script-name> such as with popular cases citing Vue.js (npx vue-cli-service), pm2 (npx pm2-runtime) and others.
Breaking down the Node.js sandbox bypass CVE-2023-30587 - A write-up that demonstrates long-time security researcher Matt Austin bypassing of Node.js own permission policies. Matt cleverly thinks outside of the (sand)box and reaches out to the Debugger capabilities that Node.js ships it, in order to workaround the limitations set by the permission policy.
NPM Ignore Scripts Best Practices - Learn about the npm ignore-scripts flag and how to use it to prevent the execution of arbitrary commands from malicious npm packages.
Time-based attacks in Prisma ORM - Services that are vulnerable to TOCTOU attacks mean that they can leak information that would then allow to disclose sensitive information. This deep-dive article from elttam provides a detailed exploration of time-based ORM leaks found in the popular open-source Prisma project.
How to exploit an API using prototype pollution - From Dana Epp’s security blog, here’s a hands-on demonstration of the dangers prototype pollution vulnerabilities hold on Node.js API servers.
How to Get a Perfect Deep Copy in JavaScript? - An experiment by Zachary Lee, who goes through the basics of shallow copies and proposes a method that cleverly uses Reflect.ownKeys(obj) to perform a deep clone without being susceptible to prototype pollution security vulnerabilities.
🔮 Node.js Tip of the Week
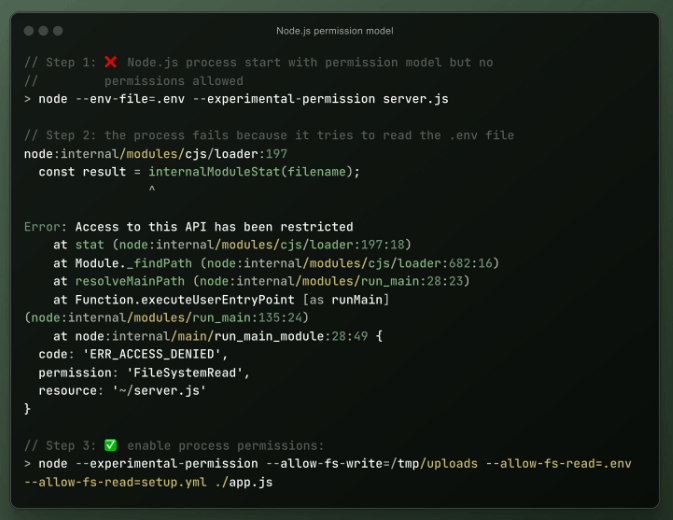
Node.js Tip of the Week: Node.js permission model Fancy some Deno-like process permissions? Node.js has those built in with --experimental-permission flag.
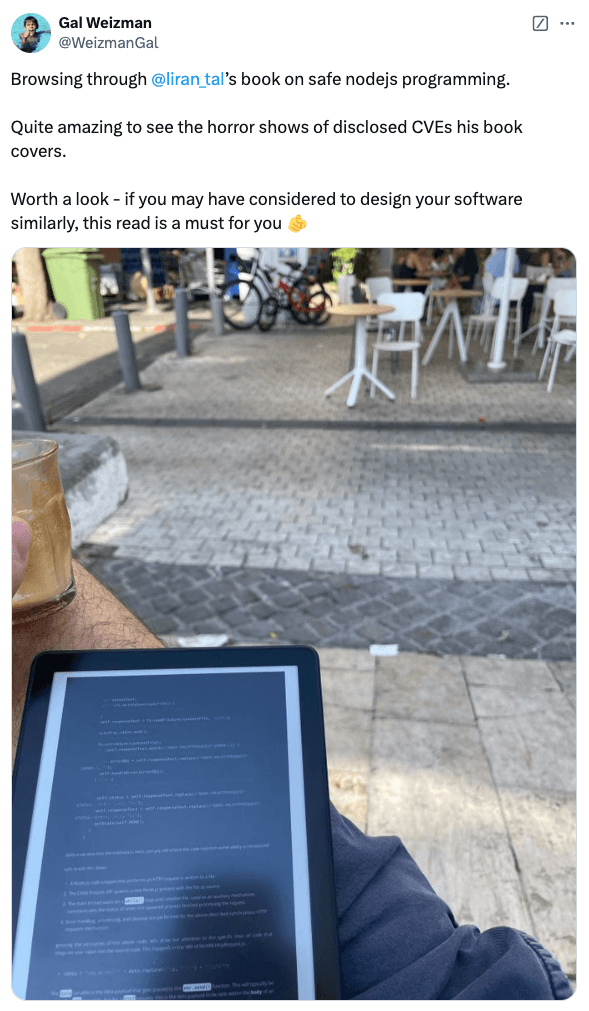
A sincere thank you to Gal Weizman, IDF Elite Computer Intelligence Unit graduate and Web Security expert at MetaMask for the kind words and support of my Node.js Secure Coding books.
📦 On npm
npm packages:
- response-time - Response time header for Node.js web applications, often used with Express as middleware.
- ts2esm - Benny’s Neugebauer’s project to help developers transform their CommonJS projects into ESM.
❗ New Security Vulnerabilities
- @directus/api found vulnerable to CVE-2025-27089 Incorrect Authorization, 19 Feb 2025
- @octokit/endpoint found vulnerable to CVE-2025-25285 Regular Expression Denial of Service (ReDoS), 14 Feb 2025
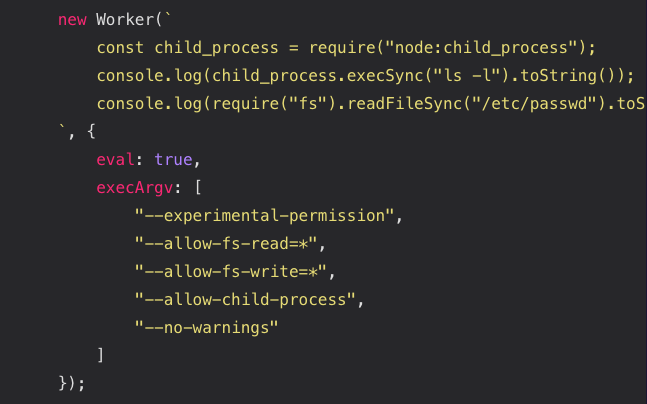
🧠 Can you find the security vulnerability here?
A friendly bug hunter I follow shared the following code snippet from their research - can you spot the vulnerability? can you suggest the exploit payload?